- Email: info@scyre.io
- Scyre LLC - 8 The Green Ste #1129, Dover, DE 19901

The attack surface is under constant change; new devices, software updates, new vulnerabilities, and device configuration changes increase risk exposure. With VM as a service, we will provide a real context for the attack surface with the recommended path to reduce the risk and follow up remediation tasks.
This service has three different options:
VM will cover your devices exposed to the internet, internal assets, and remote workers. VM as service proves a real context aligning the reports to your business processes, data flows, or locations, allowing a clear understanding of corporate exposure. With VM, you will know your top risk processes, how fast your team deploys remediations, and much more.
Listing thousands of vulnerabilities does not provide an understanding of the risk exposure. VM service deployment includes a fundamental context approach, matching the asset to your business process and services. VM Scyre service will give you the required information to decide where the effort is required to close the gap with less effort and high impact to reduce corporate risk according to the business critically.
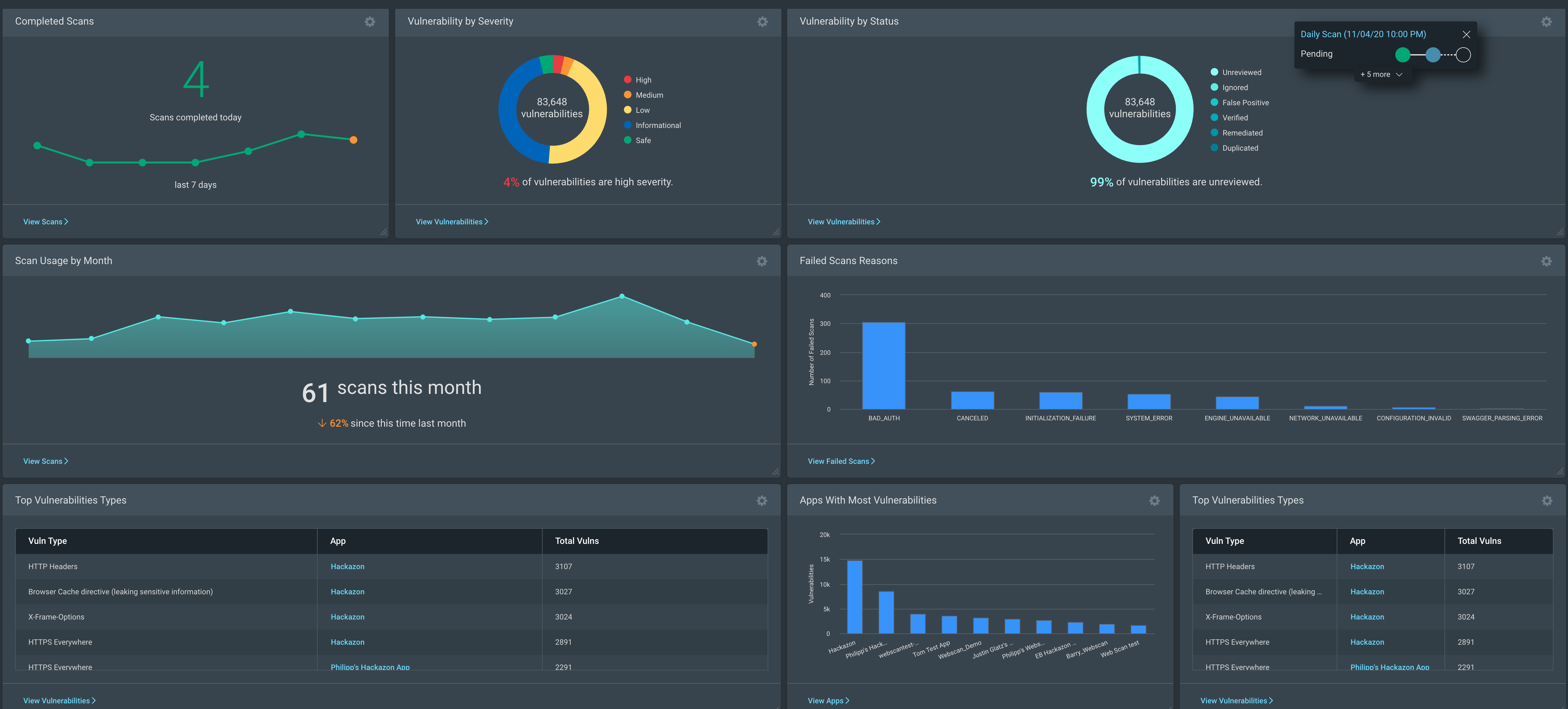
Dynamic Application Security Testing (DAST) and Runtime Application Self-Protection work together to provide accurate information about your application’s weaknesses and effortless protection until you can fix them.
Additionally, we will provide integration to your CI/CD pipeline to reinforce the SecDevops process. If you only need to run a validation scan, we can make it for you, and our report will include the critical path to remediate your app.
OT, SCADA networks, and critical infrastructure are part of an ecosystem that articulates complex processes
Read MoreDark and deep web are the treasure chest preferred by emerging threats that may target
Read MoreIdentifying malicious behaviors in the first stage of the "kill chain" requires knowledge, technology, and
Read More